Pam Beesly Sexy 2026 Storage Full Media Direct
Get Started pam beesly sexy unrivaled streaming. No strings attached on our media source. Get swept away by in a boundless collection of tailored video lists showcased in best resolution, designed for exclusive viewing aficionados. With trending videos, you’ll always have the latest info. Explore pam beesly sexy chosen streaming in incredible detail for a remarkably compelling viewing. Link up with our online theater today to view content you won't find anywhere else with with zero cost, access without subscription. Get fresh content often and dive into a realm of unique creator content developed for superior media aficionados. You won't want to miss never-before-seen footage—download fast now! Explore the pinnacle of pam beesly sexy specialized creator content with brilliant quality and exclusive picks.
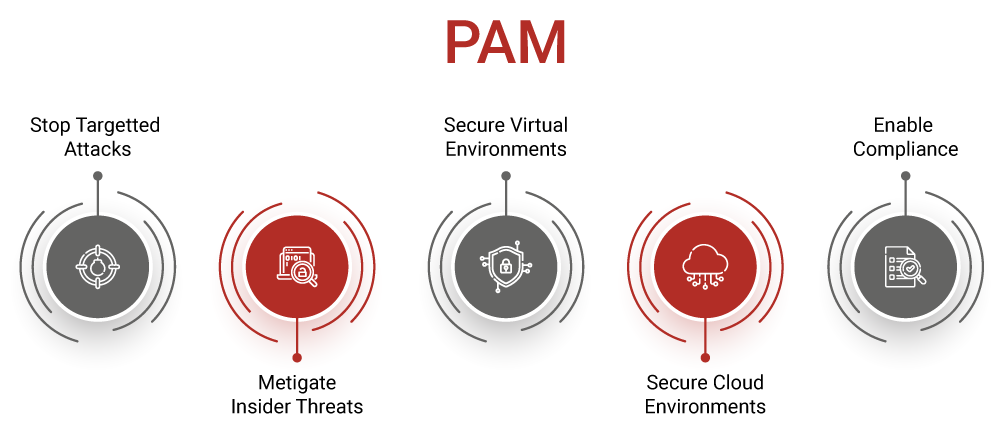
Privileged access management (pam) is an identity security solution that helps protect organizations against cyberthreats by monitoring, detecting, and preventing unauthorized privileged access to critical resources. Privileged access management (pam) is a sophisticated cybersecurity technology designed to secure, manage, and monitor privileged accounts across your it environment. Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for identities, users, accounts, processes, and systems across an it environment.
Linux PAM — How to create an authentication module | by Avi Rzayev | Medium
Privileged access management (pam) is a type of identity management and branch of cybersecurity that focuses on the control, monitoring, and protection of privileged accounts within an organization. Pam is a cybersecurity strategy and set of technologies aimed at safeguarding an organization’s most sensitive data and critical systems by meticulously controlling and monitoring access to privileged accounts. Privileged access management (pam) identifies the people, processes, and technology that need privileged access and specifies policies to secure sensitive resources in an organization
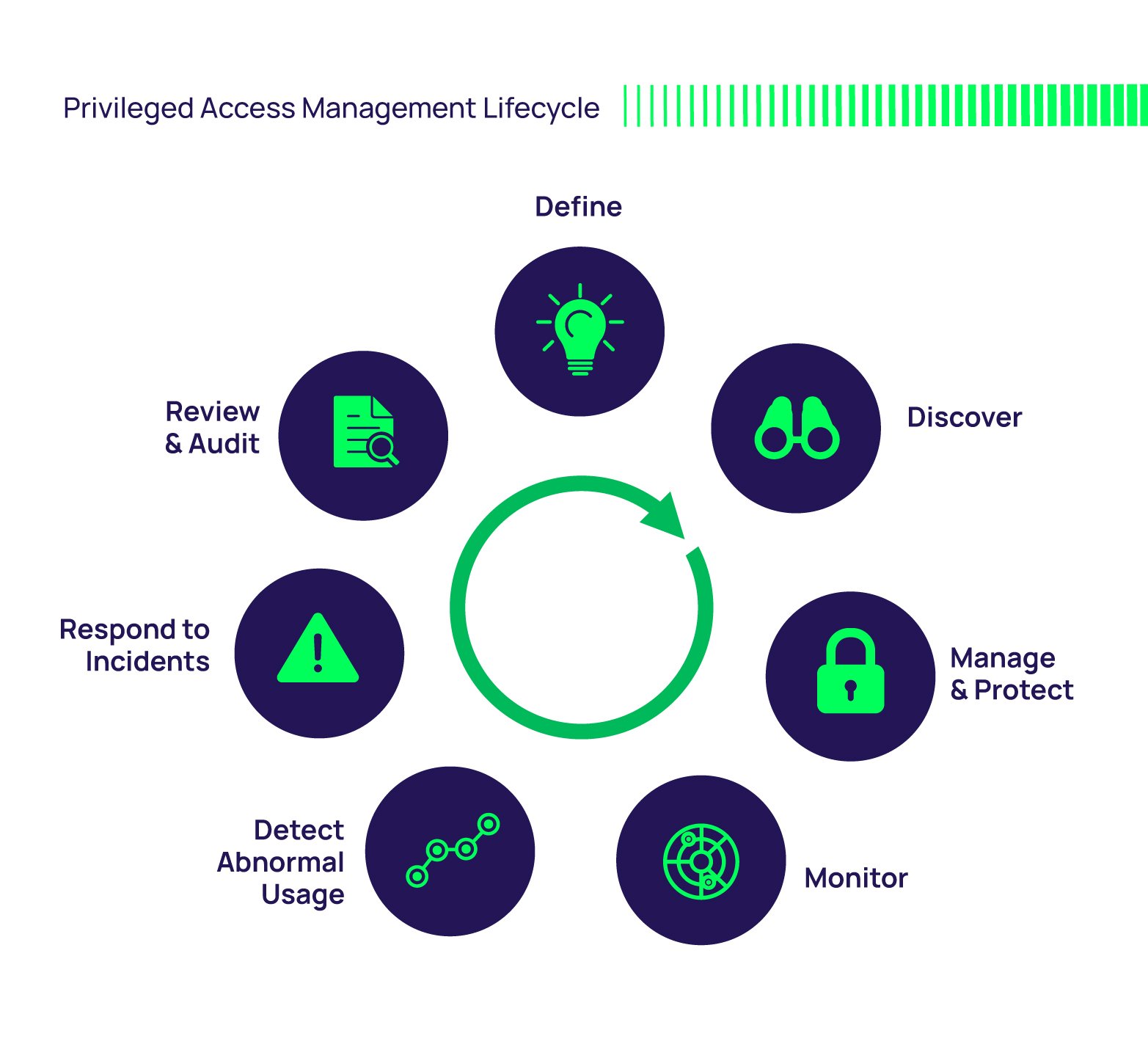
It functions across several key components to reduce risk and maintain control.
Privileged access management, or pam, safeguards access to sensitive systems and data by controlling privileged accounts